Table of Contents
- What is Secure Software Development?
- Why is Secure Software Development Crucial?
- Understanding Common Security Threats
- Compliance and Regulatory Requirements
- Conclusion
- FAQs
At Blue IT Systems, we prioritize security from the very start of the development process, ensuring that your application is built with robust, scalable, and up-to-date protection measures. Our team follows industry best practices, implementing secure coding techniques, vulnerability assessments, and regular updates to safeguard your software from potential threats.

What is Secure Software Development?
Secure software development refers to the practice of creating software with security measures integrated throughout its lifecycle. The goal is to prevent unauthorized access, data breaches, and cyber-attacks by building security into the application from the ground up. Secure development practices aim to identify and mitigate potential risks and vulnerabilities at every stage of software creation.
Why is Secure Software Development Crucial?
Cybersecurity threats are continuously evolving, with hackers finding new ways to exploit vulnerabilities in software. A single weak spot can open the door to massive data theft or system disruption. For instance, major data breaches like the Equifax breach exposed the sensitive information of millions of people due to poor security practices. By incorporating secure software development techniques, organizations can significantly reduce the risk of such incidents.
Understanding Common Security Threats
To protect your software, it’s crucial to understand the most common security threats:
- Malware
- Phishing Attacks:
- SQL Injection:
- Zero-Day Vulnerabilities:
Malicious software designed to disrupt or damage systems.
Attempts to steal sensitive information through deceptive emails or websites.
A code injection technique used to exploit vulnerabilities in a database layer of an application.
Flaws that are unknown to developers and become exploitable before they are patched.
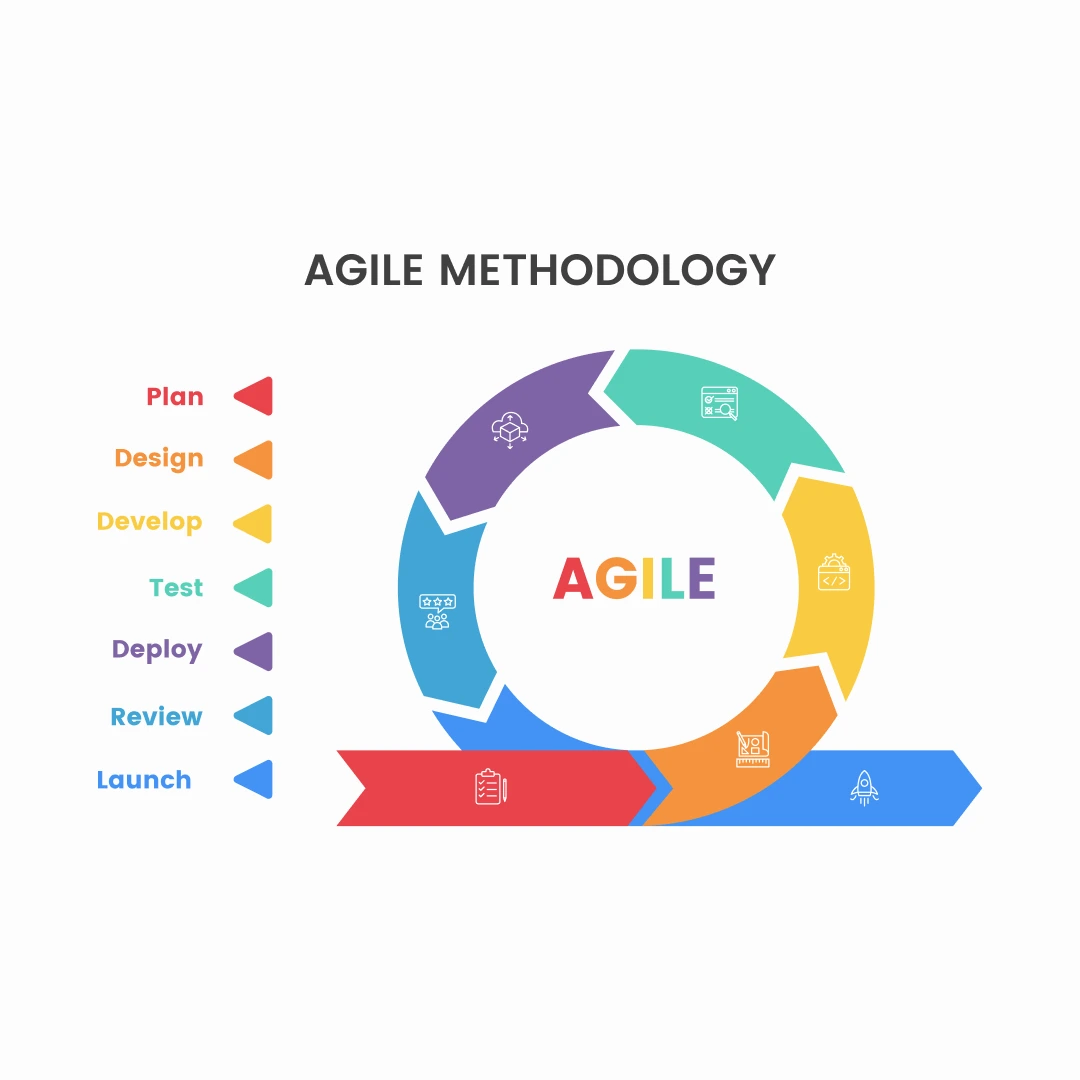
The Secure Software Development Lifecycle (SSDLC)
The Secure Software Development Lifecycle (SSDLC) is a framework that integrates security into every stage of the development process. It ensures that security is considered at each step, from initial planning to ongoing maintenance. The SSDLC follows the traditional software development lifecycle but adds an extra layer of focus on security.
Phase 1: Planning and Requirements
Security should be addressed right from the planning phase. During this stage, developers must identify security needs and conduct a thorough risk assessment. This helps to highlight potential vulnerabilities that need to be mitigated early on.
Phase 2: Design
Secure design is essential for developing a robust application. This phase includes creating a secure architecture and performing threat modeling, which involves identifying potential threats and designing solutions to mitigate them.
Phase 3: Implementation
During the implementation phase, developers should adhere to secure coding practices. This involves following coding standards and guidelines that focus on minimizing vulnerabilities like buffer overflows, cross-site scripting (XSS), and other common exploits.
Phase 4: Testing
Testing is a critical step in identifying security flaws before the software goes live. Security testing methods such as penetration testing, vulnerability scanning, and static analysis help in uncovering vulnerabilities. Regular testing is necessary to ensure that new threats are detected and resolved.
Phase 5: Deployment and Maintenance
Security doesn’t stop at deployment. Continuous monitoring is essential to detect and respond to emerging threats. Patching and updating the software to fix vulnerabilities is an ongoing process, ensuring the software remains secure over time.

The Role of Automation in Secure Software Development
Automation plays a vital role in streamlining secure software development. Automated tools can quickly identify vulnerabilities, enforce coding standards, and conduct regular security scans. Common tools like SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) help in securing applications at different stages.With Blue IT Systems, you can trust that your application is protected against vulnerabilities, ensuring the safety of your data and maintaining the trust of your users.
Secure Coding Best Practices
Here are a few best practices for writing secure code:
- Input Validation:
- Error Handling:
- Encryption:
Ensure that data input is properly validated to prevent injection attacks.
Proper error handling helps avoid exposing sensitive information.
Always use encryption to protect sensitive data both at rest and in transit.
How to Train Developers for Secure Development
Training developers on secure coding practices is essential for long-term security. Offering security-focused training programs and certifications can ensure that your team is knowledgeable about the latest threats and how to mitigate them.
Compliance and Regulatory Requirements
Secure software development must align with industry standards and regulations such as GDPR (General Data Protection Regulation) or HIPAA (Health Insurance Portability and Accountability Act). Ensuring compliance helps avoid legal issues and fines, while also enhancing security practices.

Conclusion
Secure software development is not just an option—it's a necessity in the modern digital age. By integrating security into every phase of the development process, organizations can protect their applications from a wide range of threats. Staying proactive, training your team, and utilizing automation tools are all essential for building and maintaining secure software.
At Blue IT Systems, we prioritize secure software development practices to ensure that every application we create or manage is fortified against vulnerabilities. From secure coding techniques to comprehensive security testing, our team implements robust security measures at every stage of development. Trust Blue IT Systems to safeguard your applications with solutions that prevent breaches and ensure the integrity of your software.
FAQs
- How does secure software development prevent cyber threats?
- What are the common mistakes in secure software development?
- How often should security audits be conducted?
- What is the role of encryption in secure development?
- How can small businesses ensure secure software development?
Secure software development incorporates security measures throughout the development process, reducing vulnerabilities and mitigating the risk of cyber threats.
Some common mistakes include ignoring security during the early stages, inadequate testing, and failure to keep software updated.
Security audits should be conducted regularly, ideally after each major release or whenever new vulnerabilities are discovered.
Encryption protects sensitive data by converting it into unreadable code, making it difficult for unauthorized users to access.
Small businesses can prioritize secure software development by using security best practices, conducting regular audits, and leveraging affordable security tools.